Why We need Cyber Security
In 2021, cybercrime cost the world $6 trillion. By 2025, these costs will increase to $10.5 trillion. Cybercrime is an increasingly serious problem, and to address it, strong cybersecurity is critical.Individuals, governments, for-profit companies, not-for-profit organizations, and educational institutions are all at risk of cyberattacks and data breaches. In the future, the number of attacks will grow as digital technologies evolve, the number of devices and users increase, global supply chains become more complex, and data becomes more critical in the digital economy. To minimize the risk of an attack and to secure systems and data, strong cybersecurity will be vital.
Enterprise Cyber Security
According to IBM, 77% of organizations don’t have a Security Incident Response plan, and some companies take over 6 months to even detect a breach. During this period, attackers can do everything from steal data and conduct surveillance, to damage systems and ask for ransom.Enterprise cybersecurity is a more complex approach than traditional cybersecurity, and involves protecting all enterprise assets, both on-premise and in the cloud. It also involves:
Vetting third-party providers and their security controls
Understanding the risk environment
Implementing strong access controls across the enterprise
Assessing existing vulnerabilities and threats
Taking regular data backups
Protecting assets from unauthorized access or data leaks
Implementing a remediation plan
How is Cyber Risk Measured?
Cybersecurity risk refers to the potential for loss or harm resulting from damage to an IT asset, which may lead to intellectual property theft, financial loss, reputational harm, and regulatory or legal fines. Measuring risk enables enterprises to optimize actions to manage risks better, and ensure that business objectives are not hindered.Cyber risk measurement usually involves all the following steps:
Identify and prioritize assets. Cybersecurity risk measurement starts with understanding and prioritizing the organization’s assets whose loss, exposure or damage could have an impact on operations.
Identify vulnerabilities. Any vulnerabilities that could enable a threat to cause harm are identified with automated vulnerability scanning, penetration testing, or by looking at a vulnerability database like the NIST National Vulnerability Database.
Assess the probability of a security incident. The probability that a vulnerability may be exploited is assessed, and the vulnerability is then categorized as high, medium, or low.
Calculate threat impact. The likely impact or harm that a threat may cause to an asset is calculated and categorized as high, medium, or low.
Calculate risk. Risk = Threat x Vulnerability x Asset. Based on this risk equation, the organization can measure each risk.
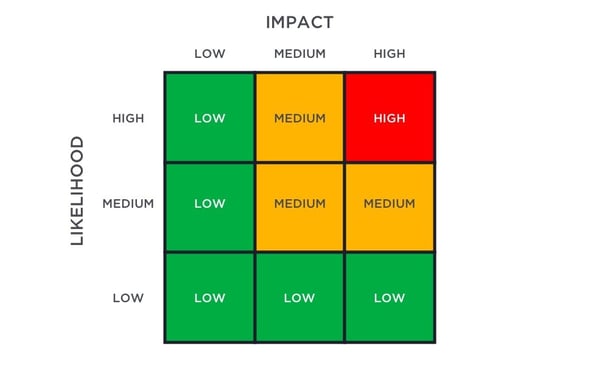
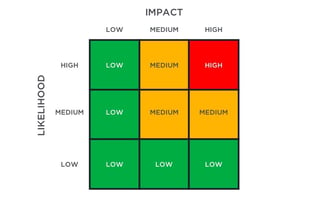
Create a risk matrix for remediation planning. Finally, the risk matrix is drawn up, with likelihood on one axis and impact on another.
Risk = Likelihood x Impact. Based on this value, each risk is categorized as high-, medium- or low-risk, following which appropriate mitigation strategies are implemented.